A screenshot of the Arkansas Division of Workforce Services' Pandemic Unemployment Assistance website at pua.arkansas.gov.
Arkansas officials confirmed last week that the state filed an insurance claim in a May 15 website security lapse that exposed sensitive data on 30,000 Arkansans seeking pandemic unemployment benefits.
More than six weeks after the state committed up to $35,000 for an investigation by a digital forensics contractor, the lapse remains a “touchy issue” to address, according to one state official involved, because an FBI investigation is still active.
The state promptly filed a claim through the Arkansas Insurance Department, according to Alisha Curtis, chief communications and legislative director of the Arkansas Department of Commerce. The local broker is BXS Insurance of Little Rock; the insurance company is Star Indemnity of New York. Curtis added that no value has yet been placed on the claim. “It’s early,” she told Arkansas Business in an email.
Gov. Asa Hutchinson has depicted a tipster’s actions in exposing the website problem as an “exploitation” and a “breach” of the state’s computer system, using language significant to the insurance provisions.
“The state is covered through cyber security insurance,” Curtis said. “The claim the Insurance Department made was through Star Indemnity, and from there they may hire various vendors such as Clark Hill (legal firm) who specialize in data incidents.”
Clark Hill, based in Chicago, joined the Commerce Department’s Division of Workforce Services in directing Tracepoint LLC of New Orleans, the investigative contractor, to dig into state computer logs and analyze the May 15 data compromise of the state’s Pandemic Unemployment Assistance website.
Workforce Services signed a deal in mid-May for Tracepoint to determine how personal data — including Social Security and banking numbers — became visible on the site. “Unauthorized access” was the cause of the claim, according to a state cyber-liability insurance loss document.
The state pays $296,359 in annual premiums for a $10 million cyber insurance policy. Curtis said Tuesday that Clark Hill consults with the state on insurance matters, and that the firm helped initiate Tracepoint’s investigation.
The Tracepoint contract called for a technical analysis of computer systems “and pertinent logs to identify evidence of unauthorized access or exfiltration of sensitive data.” A cost estimate, excluding reimbursable expenses, totaled $20,625 for a minimum of 55 hours of work, up to $35,625 for 95 hours.
A “statement of work” between Tracepoint and the state, signed by DWS Director Charisse Childers and Stacey Levy of the New Orleans contractor, promised to identify any evidence of data being changed or extracted from the site, and to determine whether anyone took advantage of the vulnerability. Tracepoint’s inquiry, for now, is considered part of the ongoing FBI investigation, Curtis said, meaning that it’s off limits for discussion by state officials.
State Commerce Secretary Mike Preston told legislators in May that he couldn’t answer questions on the website inquiry. Curtis offered a statement:
“The Department of Commerce is cooperating with the FBI on its investigation into the recent data security incident,” it said. “We believe law enforcement should perform their investigations uninterrupted or unencumbered by the department. Due to this investigation, we are limited in the information we can share at this time.”
Curtis said the site, which was taken down May 15 after the vulnerability was exposed, was secured before being restored to the web on May 20. “The problem was corrected,” she said, and though she didn’t know technical details about security enhancements, she called them “strong.”
Rushing to Get Money Out
At a May 27 meeting of the Arkansas Legislative Council in Little Rock, Childers, Preston and DWS Chief Information Officer Carter Hawkins said that an aging unemployment insurance computer system and the desire to get money out quickly during the coronavirus pandemic contributed to the website’s security problems. The site was created to provide unemployment benefits to self-employed workers and independent contractors ineligible for regular unemployment payments.
The site was put together quickly by Protech Solutions LLC of Little Rock, an existing state IT contractor, under a $3 million contract with contingencies that could add $2 million to the final total.
A computer programmer told the Arkansas Times, which broke the story of the vulnerability, that he’d noticed sensitive data was visible while navigating the site to file for benefits. Private data was exposed for about 30,000 applicants, all of whom had to revise their passwords when the site reopened five days later.
The programmer told the Times he’d reported the threat to several state agencies before turning to the press.
Gov. Hutchinson cast suspicion on the tipster, suggesting he’d “exploited” the website, and reported that the FBI had opened an inquiry. In a May news conference, the governor said his use of “exploitation” referred to actions including someone simply viewing sensitive information without authorization.
Cybersecurity experts compared that to blaming the messenger. Ted Clouser, president and CEO of PCA Technology Solutions of Little Rock, praised the state for responding quickly, but he said the person reporting the vulnerability, as he understood the situation, was a “good Samaritan.” “If I came to your office and let you know that your back window wasn’t locked and that I was able to stick my head in and look around, it doesn’t mean there was a burglary,” Clouser said.
The Insurance Department’s “Cyber Liability Insurance Coverage Overview” defines a privacy breach, in part, as “the unauthorized acquisition, access, use, or disclosure of Personally Identifiable Non-Public Information, which compromises the security or privacy of such information … .”
Connor Hagan, an FBI spokesman, said Tuesday the bureau had released no new statements on its inquiry. “At this time, all I can say is that the FBI Little Rock office is investigating this recent cyber incident related to the Arkansas Pandemic Unemployment Assistance website. I can’t discuss any details regarding our ongoing investigation.”
‘Thousands of Lines of Code’
Preston, in his remarks before lawmakers, said all applicants on the site who filed before May 15 received state notifications on how to enroll in credit monitoring. “The site is continuing to process claims on a daily basis and we’re sending disbursements,” he said.
The forensic examination and FBI inquiry involved going over “thousands of lines of code,” Preston added, promising to share more information “when appropriate.”
Protech, which designed and built the PUA website, has a long-term contract to run Arkansas’ child support information system. That contract, signed in 2016 and extending through next year, is worth $42 million.
Because Protech was already doing business with the state, DWS was able to use emergency procurement rules to rush the site construction. Childers told lawmakers last month that whether she would choose to use Protech again would depend on whether other vendors were eligible under emergency rules.
Hawkins, the Workforce Services CIO, told legislators that the Protech contract included “language concerning data security and data breaches and responsibility,” but he added that “those consequences have not been addressed yet.”
Pandemic Unemployment Assistance Through June 29
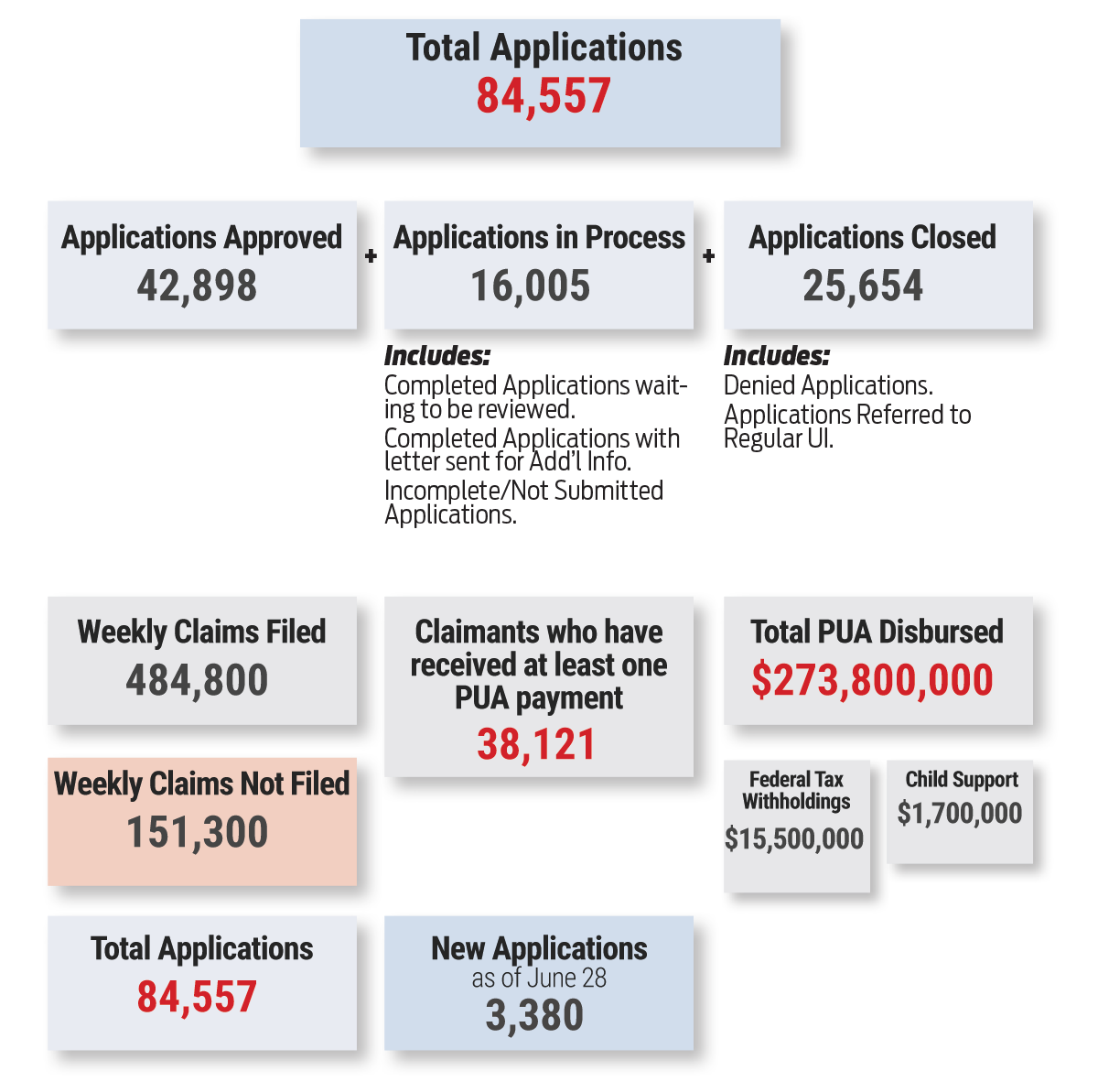
| Applications Approved | |
| STATUS | APPLICATIONS |
| Approved (Eligible for Retro) | 42,898 |
| Total | 42,898 |
| Applications in Process | |
| STATUS | APPLICATIONS |
| Incomplete Application | 8,938 |
| Completed -Pending Review | 4,946 |
| Requires Add’l Information | 2,121 |
| Total | 16,005 |
| Applications Closed | |
| STATUS | APPLICATIONS |
| Referred to Regular UI | 13,244 |
| Fraud Review | 6,504 |
| Denied | 5,841 |
| Invalid Applicaton | 65 |
| Total | 25,654 |
| All Weekly Claims Filed Through June 29 | ||
| CUSTOM | CLAIMANTS | CLAIMS COUNT |
| Approved Payment Pending | 6,773 | 21,707 |
| Approved-Paid | 33,914 | 432,124 |
| Filed – Pending Review | 1,000 | 3,050 |
| Filed-Not Eligible for Week | 11,254 | 27,886 |
| Not Filed | 19,813 | 151,302 |
| Total | 72,754 | 636,069 |
| Weekly Claims Filed, Last Week of June | ||
| CUSTOM | CLAIMANTS | CLAIMS COUNT |
| Approved-Paid | 959 | 9,444 |
| Filed-Not Eligible for Week | 122 | 286 |
| Filed – Pending Review | 81 | 383 |
| Approved Payment Pending | 54 | 198 |
| Total | 1,216 | 10,311 |












